Azure Active Directory | Authentication Policies
Microsoft has announced that legacy multifactor authentication and self-service password reset policies will be deprecated in January 2024. The new Microsoft Entra Admin center will provide with a wizard to migrate the legacy policies to the new Authentication methods policies.
Legacy policies
| Multifactor authentication policy | Authentication method policy |
|---|---|
| Call to phone | Voice calls |
| Text message to phone | SMS |
| Notification through mobile app | Microsoft Authenticator |
| Verification code from mobile app or hardware token | Third party software OATH tokens Hardware OATH tokens (not yet available) Microsoft Authenticator |
The policies above are tenant-wide and there is no need for user or group information. Every user gets the same options.
| SSPR authentication methods | Authentication method policy |
|---|---|
| Mobile app notification | Microsoft Authenticator |
| Mobile app code | Microsoft Authenticator Software OATH tokens |
| Email OTP | |
| Mobile phone | Voice calls SMS |
| Office phone | Voice calls |
| Security questions | Not yet available; copy questions for later use |
Authentication methods policy
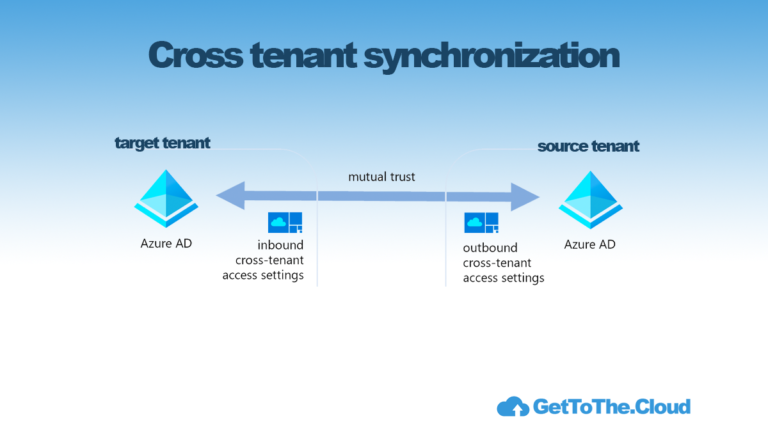
With Microsoft Entra you will be able to navigate to Azure Active Directory -> Protect & secure -> Authentication methods. You will find by default all the policies disabled. But there is also an option to migrate current policies to the new authentication policies. It is still in preview but it already works like a charm.
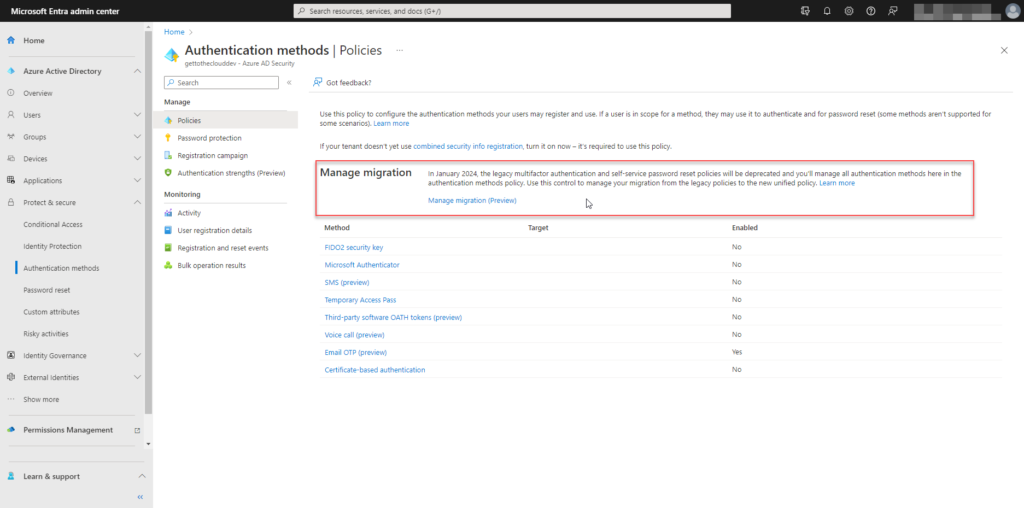
Enabling the new authentication policies, can have a huge impact. Therefore Microsoft enables to respect the legacy (tenant) policies and run the new policies for the users that do not match the new policies. Users will be able to change there authentication themself.
New additions to these policies are FIDO2 security key, Temporary Access Pass, and Azure AD certificate-based authentication. With these policies the setting can be defined to a user or a group or all users. It is possible now to enable multiple multifactor or more secure for high risk users.
Microsoft recommends passwordless authentication methods such as Windows Hello, FIDO2 security keys, and the Microsoft Authenticator app because they provide the most secure sign-in experience. Although a user can sign-in using other common methods such as a username and password, passwords should be replaced with more secure authentication methods.
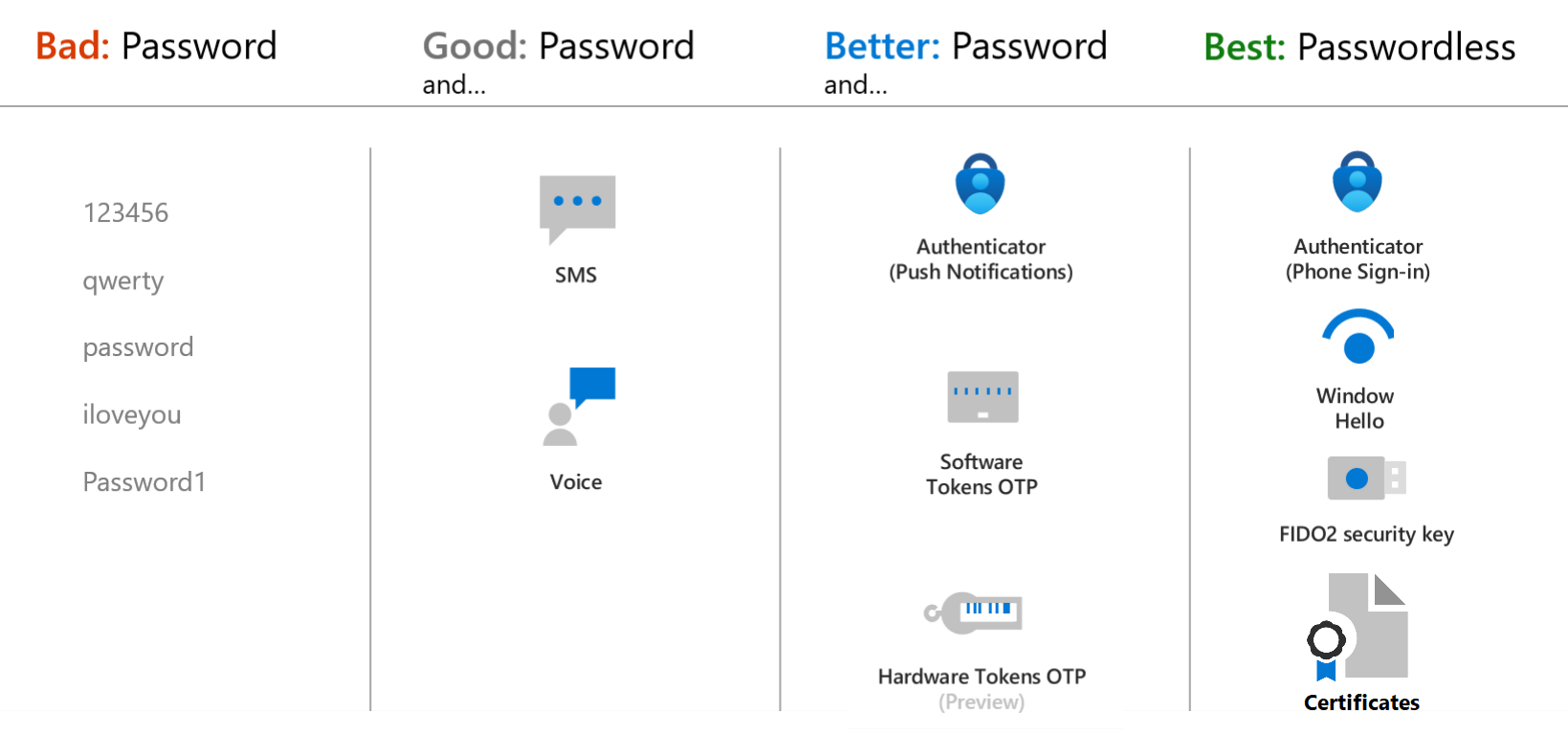
The Microsoft Authenticator app can be enabled for passwordless sign on.
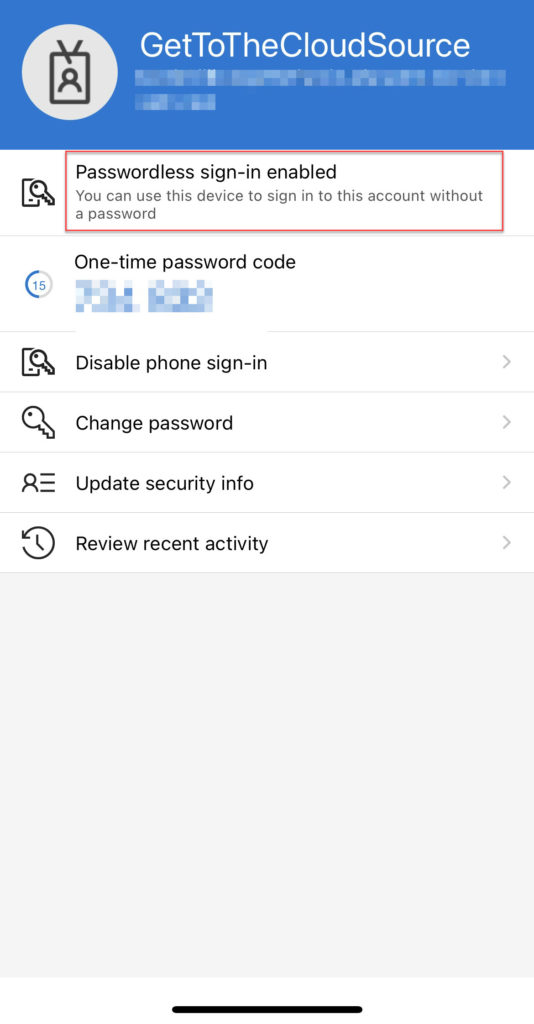
Open the Authenticator App and select the user account that is configured. Select Passwordless Sign-in enabled and follow the signin.
If it is configured correct, when browsing to https://portal.office.com. Enter here the username and click next. A password prompt will appear.
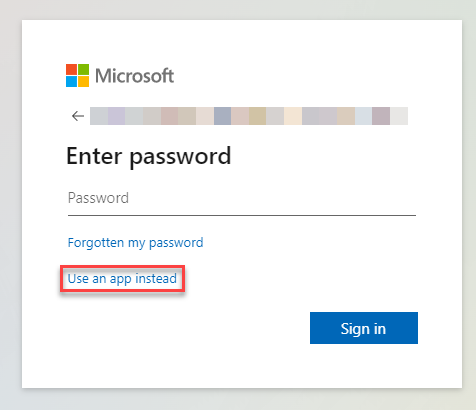
Select here Use an app instead
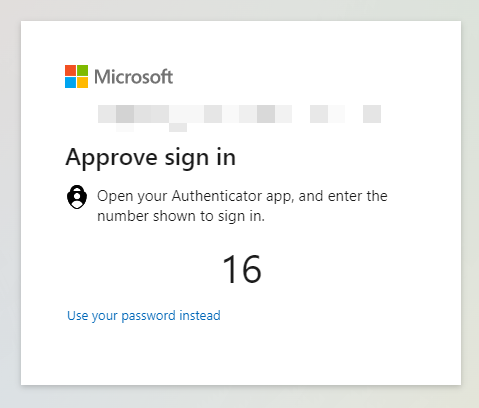
Opening the Authenticator app will give a new prompt
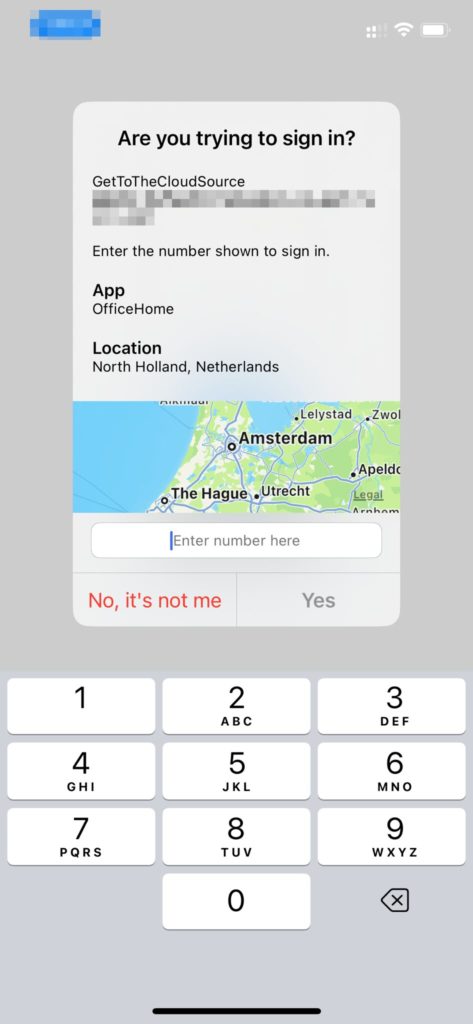
Entering the number showing on the browser, will automatically sign-in the user.
Configuration options
In Microsoft Entra Authentication Policies will give you the possibility to change the policy for passwordless sign-in.
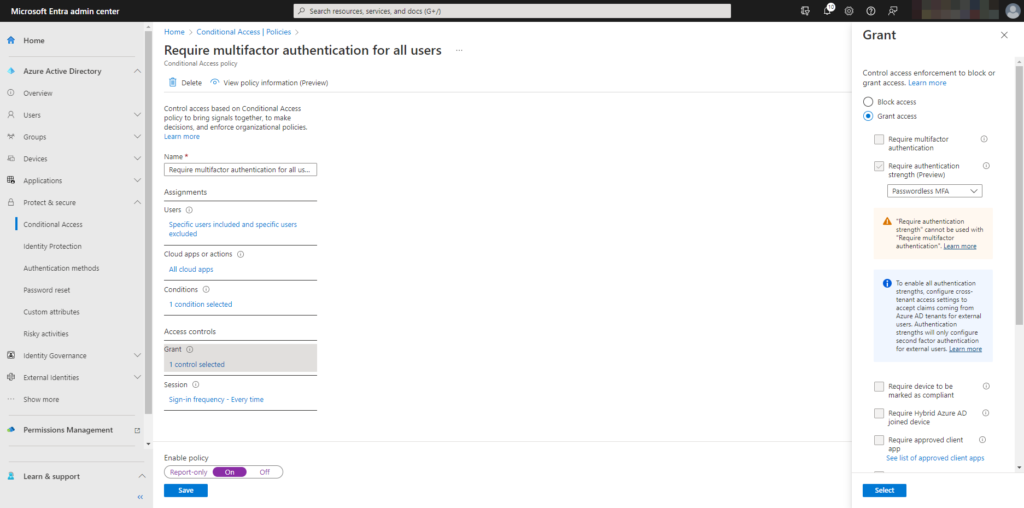
Of course you will be able to configure the policy through Microsoft Graph API.