Azure | Secure Azure Virtual Desktop with MFA
Read also the updated version: Azure | Secure Azure Virtual Desktop with MFA !!UPDATE!! – GetToTheCloud
In Azure | Deploy Azure Virtual Desktop – GetToTheCloud we have seen how to setup Azure Virtual Desktop for multiple users with a multi-session Windows 11 image. But when you are using Azure Virtual Desktop, you would like to secure also the access to the desktop. In this blogpost we will use Azure Mutli-Factor Authentication for this.
In Januari 2024 the new Azure Authentication Policies will be the default as I described before in Azure Active Directory | Authentication Policies – GetToTheCloud. Let’s use those policies to enable a more secure way to access the Azure Virtual Desktop.
Understanding Conditional Access
Conditional access allows you to set conditions that must be met before a user can access a resource. For example, you might require that a user is accessing a resource from a trusted device or network location. In the case of AVD, you might require that users can only access their virtual desktops from trusted IP addresses.
To set up conditional access for AVD, you’ll need to create a conditional access policy in Azure Active Directory (AD). This policy can then be applied to AVD resources to require that users meet specific conditions before they can access their virtual desktops.
Enable the Microsoft Authenticator App
In Microsoft Entra we first need to enable the Microsoft Authenticator App for using it in the new Conditional Access policies.
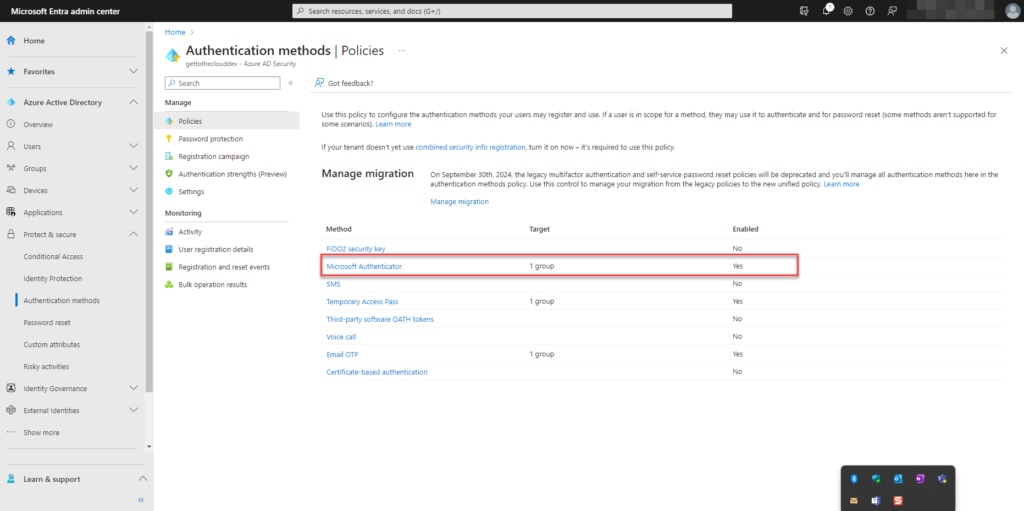
Clicking on Microsoft Authenticator will open a new dialog
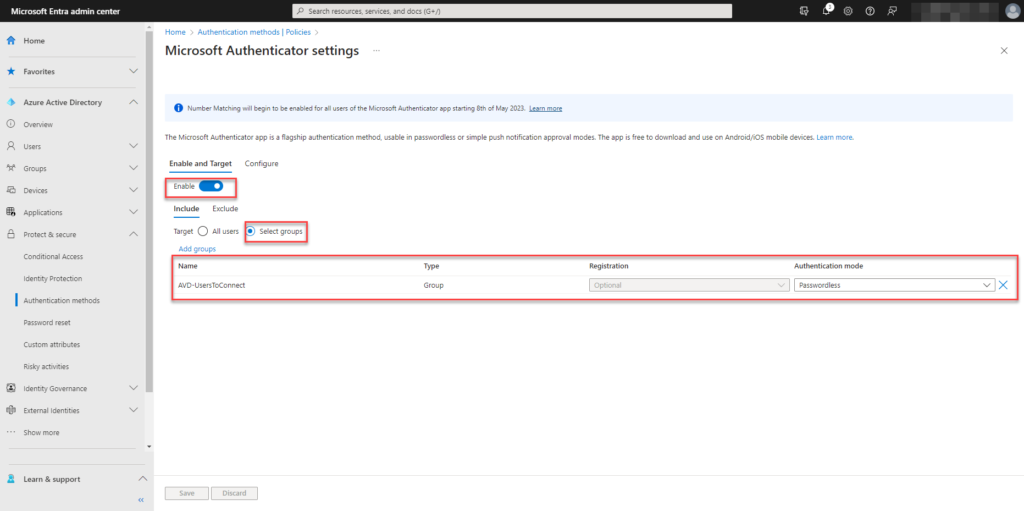
Add here to the INCLUDE the group with your Azure Virtual Desktop users. For authentication method use Passwordless
At the tab CONFIGURE we have also enabled all the options and added the same group to the include:
- Require number matching for push notifications
- Show application name in push and passwordless notifications
- Show geographic location in push and passwordless notifications
- Microsoft Authenticator on companion applications
Now that the Authentication Policy is set, we can setup the conditional access policy.
Conditional Access Policy
In Microsoft Entra you can setup the Conditional Access policies. Click on + Create new policy to get started on setting up a new policy.
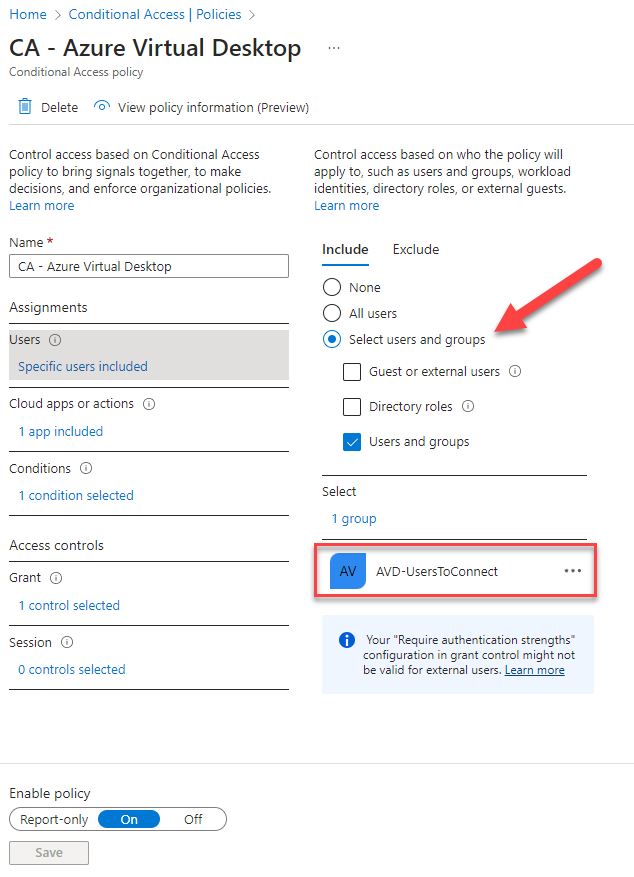
Enter a name. With the users assignment select Select users and groups at the INCLUDE tab. Add the group with your Azure Virtual Desktop Users.
Moving on the Cloud apps or actions
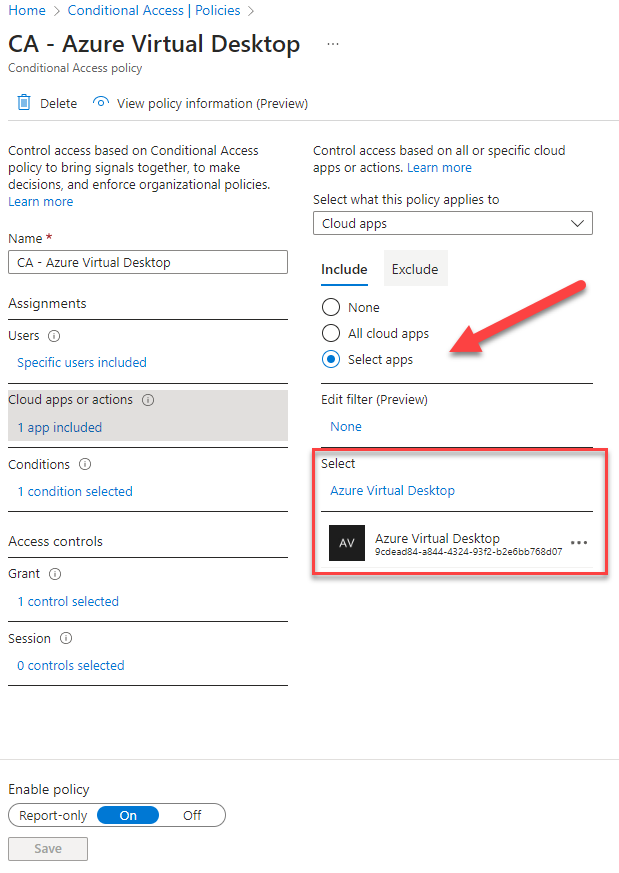
Select Select Apps and add Azure Virtual Desktop
Moving on the Conditions
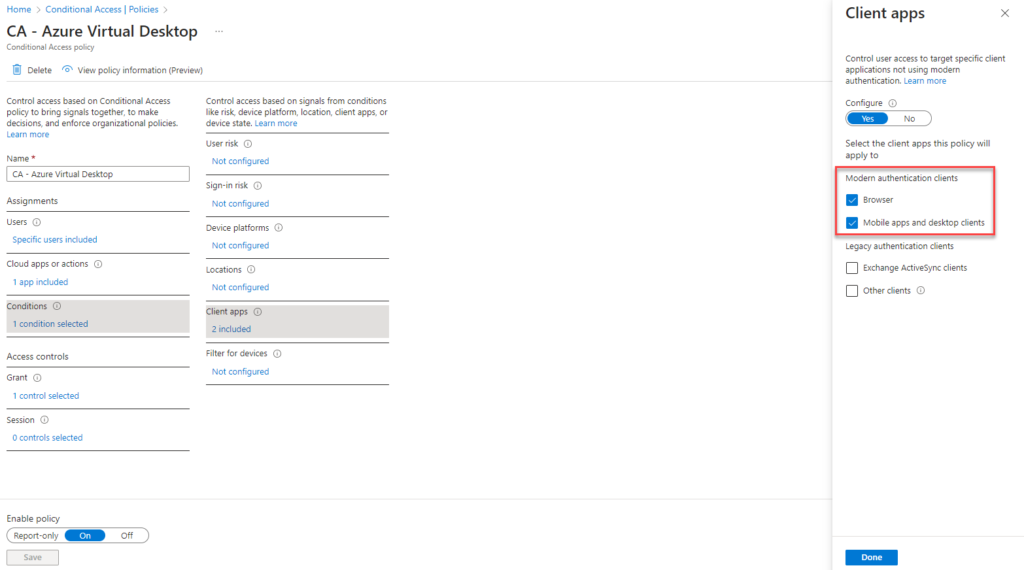
Add the Client Apps for MODERN AUTHENTICATION CLIENTS
At Access Control – Grant we do the final setting

By default the Enable policy will be set to Report Only. If you are sure about your settings, you can set it to On.
Microsoft Authenticator Setup
Browsing to https://aka.ms/mfasetup, the user will be able to add the account to the Authenticator App on their phone. This will be also giving them the option to login passwordless.
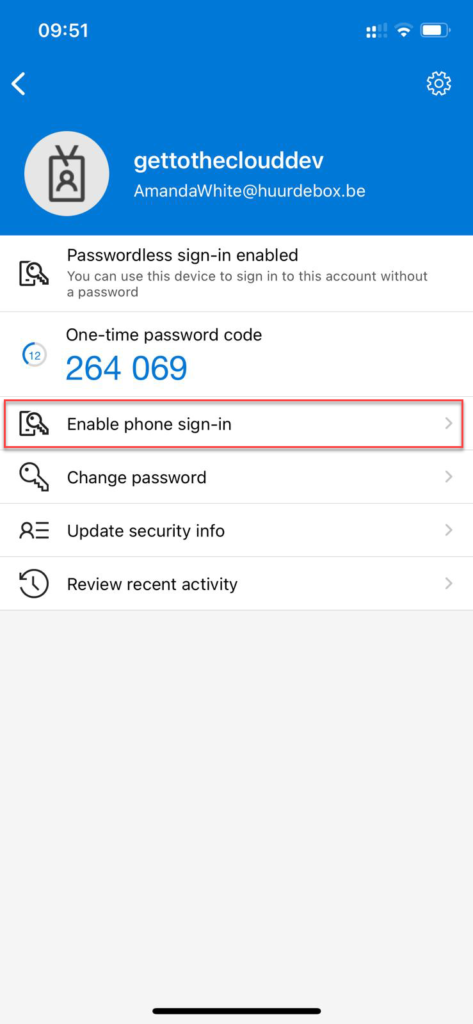
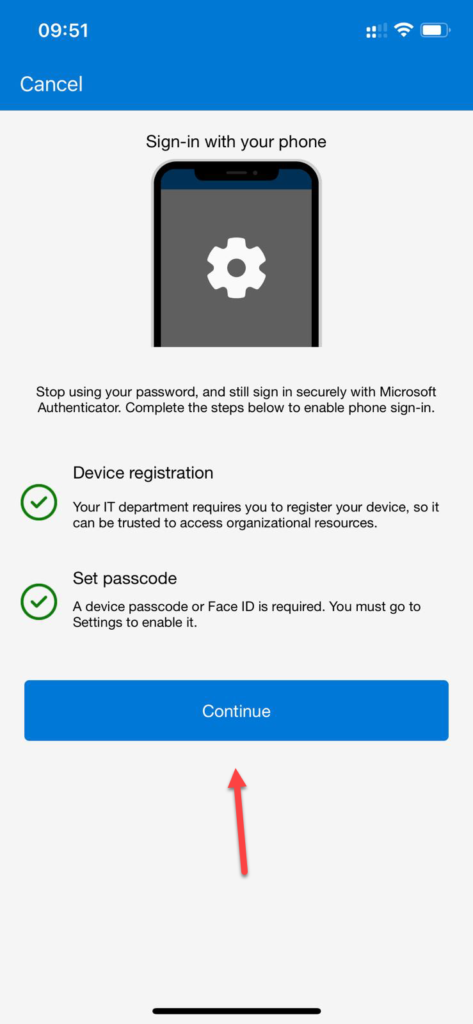
Click on Enable phone sign-in and click on Continue. After completing the authentication you will see in the app that Enable is changed in Disable.
Browsing now to https://client.wvd.microsoft.com/arm/webclient/index.html will give a login prompt. Entering the e-mail address will give an extra option:
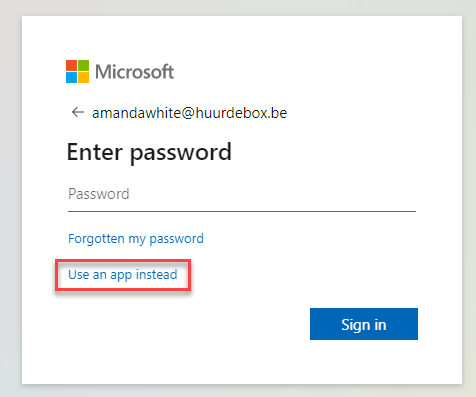
Using the option Use an app instead will give a PUSH notification on the phone where the account was added to the Authenticator App.
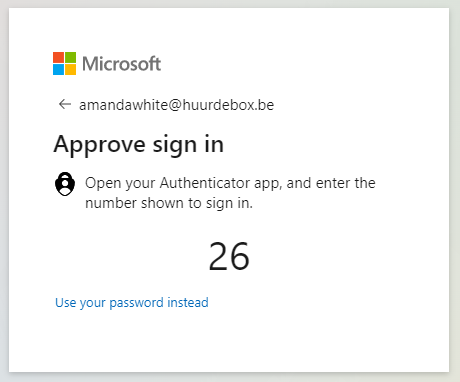
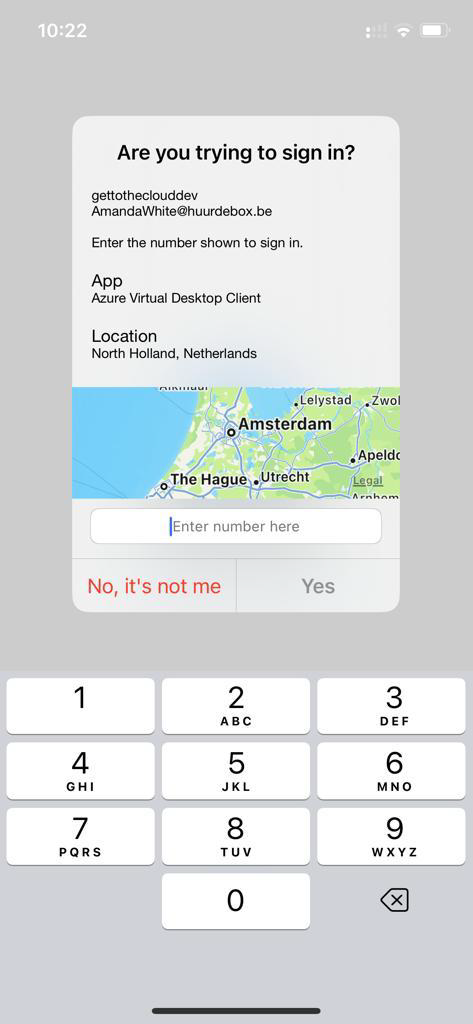
Entering number 26 in the App will authenticate me and I did not use my password for the user.
Connecting will result in: