E-Mail | Security setup SPF
These days security officers are struggling securing the e-mail and prevent that snooping or MTM (Man in The Middle) attacks. There are various protocols available to secure the e-mail.
You can use SPF, DKIM or DMARC for securing the e-mail traffic over the internet. The protect against phishing, spam, viruses and other malware by securing the sender (e-mail address/domain), the sending host (mail system) and the authenticity (contents) of an e-mail message. Enabling the standards involves adding records to the domain name’s DNS details. Also is a MTA-STS a possibility to help. Let’s deep dive in SPF.
SPF (Sender Policy Framework) records is a standard to help your battle against spam. It is an email authentication standard that protects senders and recipients from spam, spoofing and phishing. By adding this record to your domain, you will provide a list of senders that are approved to send e-mail from your domain.
Why?
You can still send emails without setting up SPF, but having an SPF policy provides an additional trust signal to ISPs so you can increase the likelihood that your emails reach your recipient’s inbox.
SPF won’t solve all of your delivery problems, but it’s an additional layer that, combined with standards like DKIM and DMARC, can improve your delivery rates and prevent abuse.
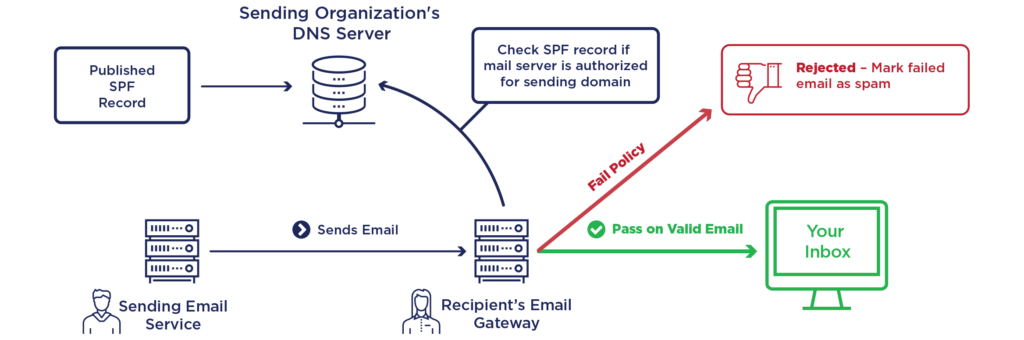
How does SPF work?
SPF Records might look like complicated and confusing, but they are fairly easy to understand once you know the basics. An example of a SPF record:
v=spf1 a mx include:spf.gettothecloud.eu ~allLet’s look at the key elements:
The “a” element:
Let’s say that I send mail from IP 57.54.22.137 for the domain “gettothecloud.com”. If “gettothecloud.com” has an A record that returns 57.54.22.137 then this mechanism will pass.
The “mx” element:
Any domain that hosts e-mail has one or more MX records. These records define which email servers can relay email. For example if you use Microsoft 365, there is only one record with the MX and priority 0. This will be the host where the e-mail can be delivered.
The “include” element:
Let’s say that I send mail from IP 57.54.22.137 for the domain “gettothecloud.com”. If the SPF record for “gettothecloud.com” includes spf.gettothecloud.eu and 57.54.22.137 passes against the SPF record for spf.gettothecloud.eu, this mechanism will pass.
The “all” element:
The “all” mechanism will match against everything, and in this case, the result will be a SoftFail for everything that gets to this point.
Setting up an SPF record
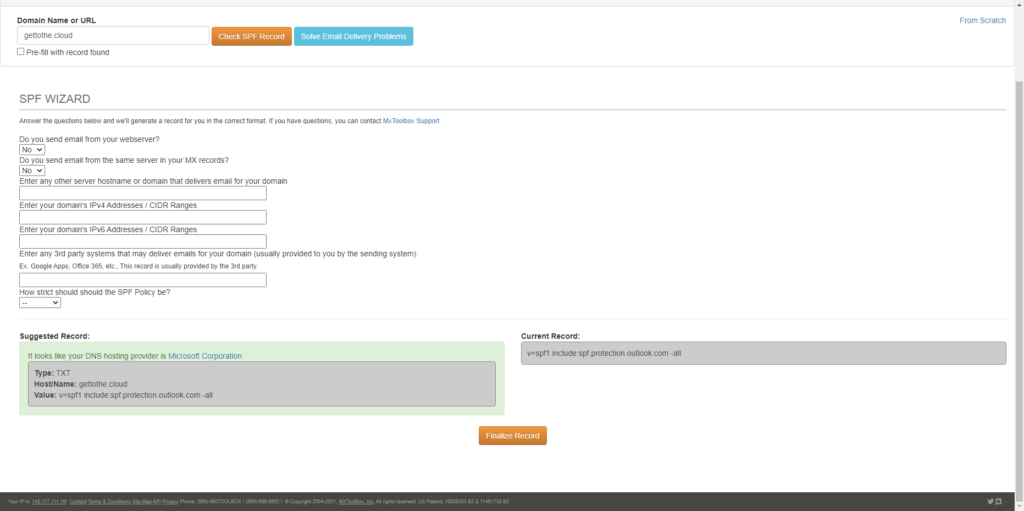
First before you can setup an SPF record on your domain, you need to decide which hosts will be allowed to send e-mail from your domain. If you have done that you can browse to https://mxtoolbox.com/SPFRecordGenerator.aspx to discover first your current SPF record and then use the wizard to generate an new record.
This record can be copied and paste at your DNS settings with your domain provider.