Azure Active Directory Assessment | Part I
Setting up Azure Active Directory is one thing, but managing is a whole other thing. With multiple administrators it is hard to keep the Azure Active Directory
Multiple administrators are instructed often how to use a name convention or how to use create groups or users. Mostly they are in a rush and doing administrator tasks on the spot, without maintaining the guidelines.
The creation of App registrations is by default enabled for all users and as an administrator you will not get a notify of that. Applications need permissions to access the Azure Active Directory and it is not audited. Clicking in the portal is a way to go but wouldn’t it be nice if you just run a script and get a detailed report about it.
What to assess
Getting reports from Azure Active Directory is getting a lot of information. A lot of information to process and to review. I Personally would like the following information:
- Users (Member/ADSynced/Guest) and their attributes
- Groups (Security/Distribution/Unified) and their attributes and members
- Licensing (Assignments/enabled)
- Organization Details
- App registrations with Token lifetime/certificate lifetime
- Azure AD Roles included members and if are eligible (Azure P2 license)
- Conditional Access policies and settings
- Devices (Registered/AAD Joined)
Enable M365 option
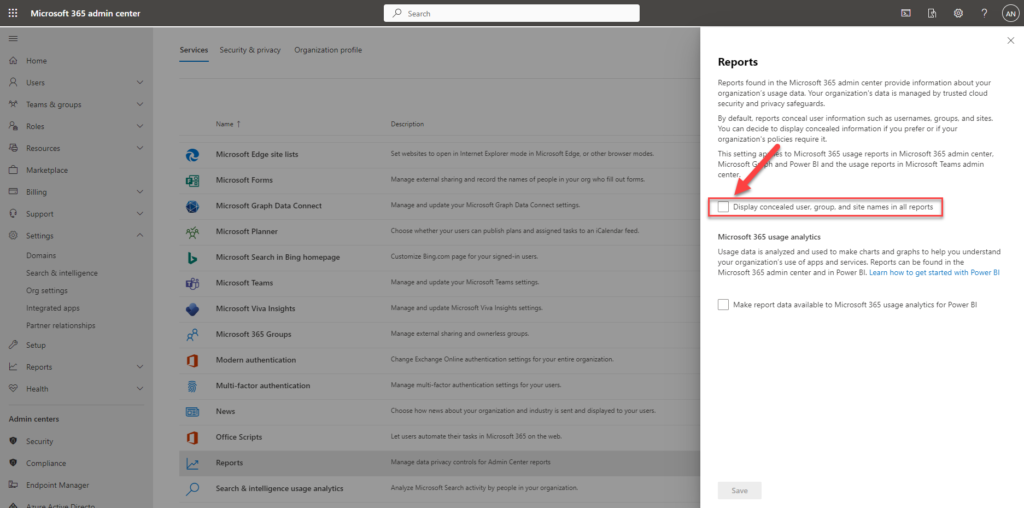
By default the reports from M365 do not have any personal information. userPrincipalName en DisplayName are random numbers in a report. To avoid that you have to disable a checkbox in the portal.
Browse to : https://admin.microsoft.com/#/Settings/Services/:/Settings/L1/Reports
How to get the information
I Use Microsoft Graph API to get the information. The cmdlets within Azure PowerShell modules are going to be deprecated within time and the Graph API will remain.
To use the Graph API, you will need an App registration with the correct permissions. Application assigned permissions we are going to use:
| user.read.all (application) | directory.read.all (application) |
| group.read.all (application) | application.read.all (application) |
| auditlog.read.all (application) | orgcontact.read.all (application) |
| policy.read.all (application) | userauthenticationmethod.read.all (application) |
| reports.read.all (application) | rolemanagement.read.all (application) |
| rolemanagement.read.directory (application) | identityriskevent.read.all (application) |
| device.read.all (application) | identityprovider.read.all (application) |
| organization.read.all (application) |
To get to know which permissions are needed, you will find them in the reference guide at the Microsoft docs or using the Graph API explorer.
Also you will need the URL from Graph API to get the correct information. A good way to start is the Graph Explorer and login with your admin credentials.
In the next post, an App registration will be created with the correct permissions. The credentials and connection details will be saved to the Desktop of the user that is creating the app. The app registration will not use a certificate, but is using a client_secret so it can be run on another computer as well.